CVE-2018-5798 – Cross-site scripting vulnerability in Cloudera Manager – Part 1
Author: Shafeeque Olassery Kunnikkal | Category: Cross Site Scripting, CVE-2018-5798, Cyber Security, Vulnerability Assessment | Leave a Comment
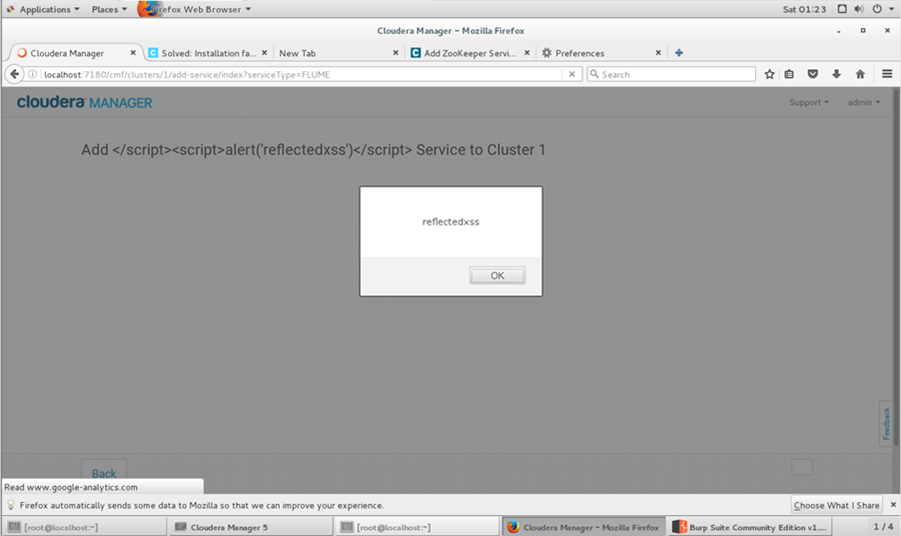
Below is the details of the reflected XSS , I have found in Cloudera Enterprise. There were multiple XSS was reported and will be publishing this details in subsequent posts. More details can be found here :-
Login to Cloudera manager using credentials
admin:admin or cloudera:cloudera
We need to intercept the HTTP traffic so launch Burps suite. Set the proxy in browser 127.0.0.1, port 8080
Click on add services against the cluster in Cloudera Manager, select any service, Let me choose the service as flume.
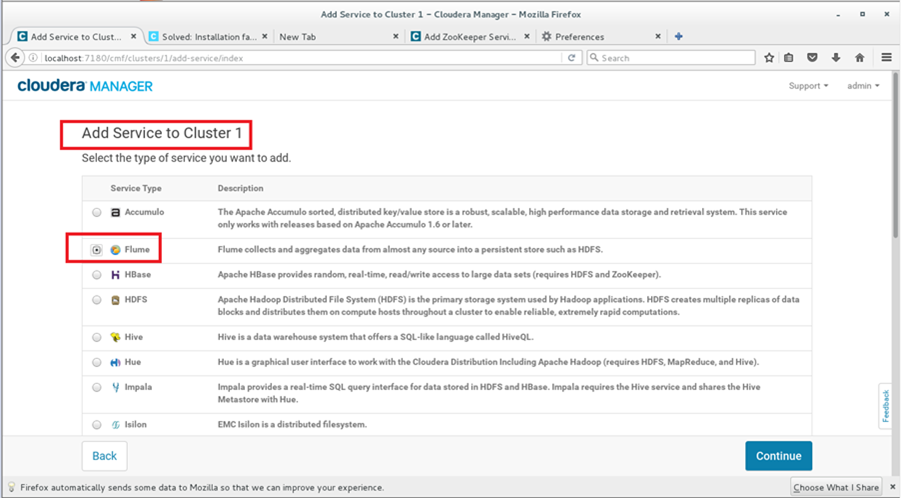
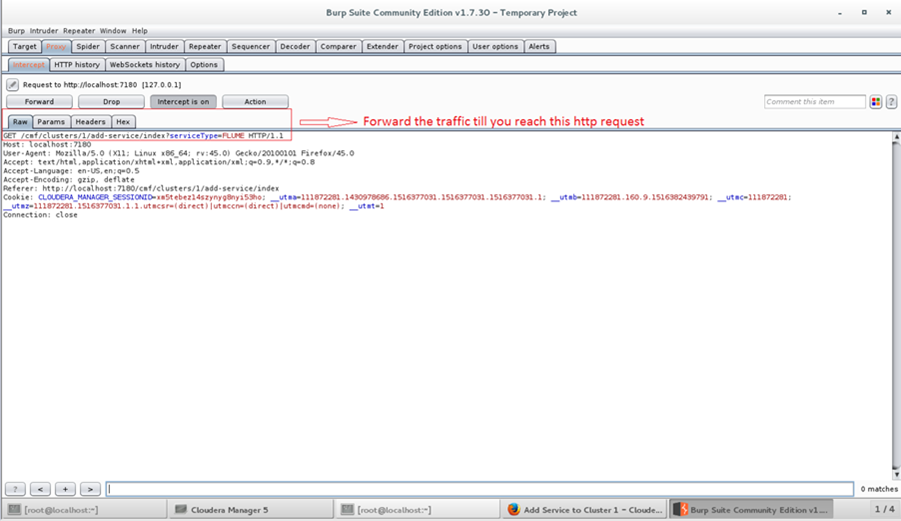
Click continue, the traffic will be intercepted in browser.
Click forward of the proxy traffic tab in the burp till you get the request as shown in the image.
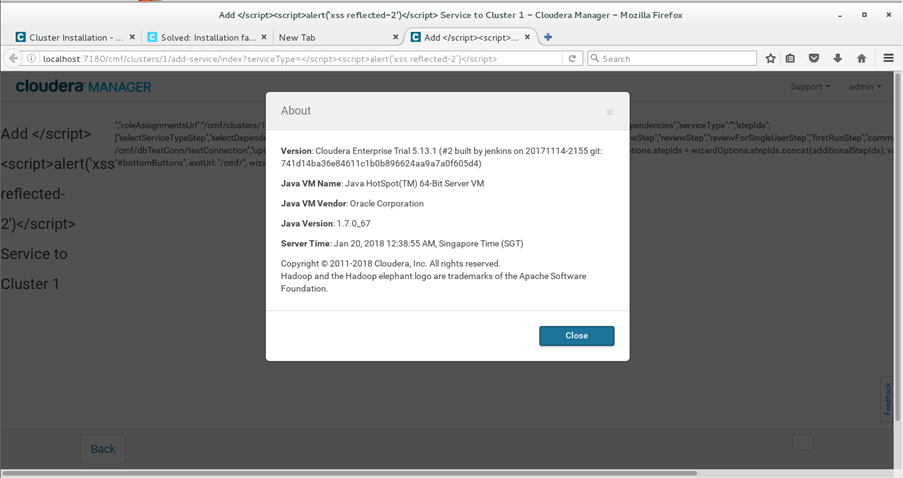
Now we want to inject the XSS payload in the parameter ‘ServiceType’ as shown in the following image.
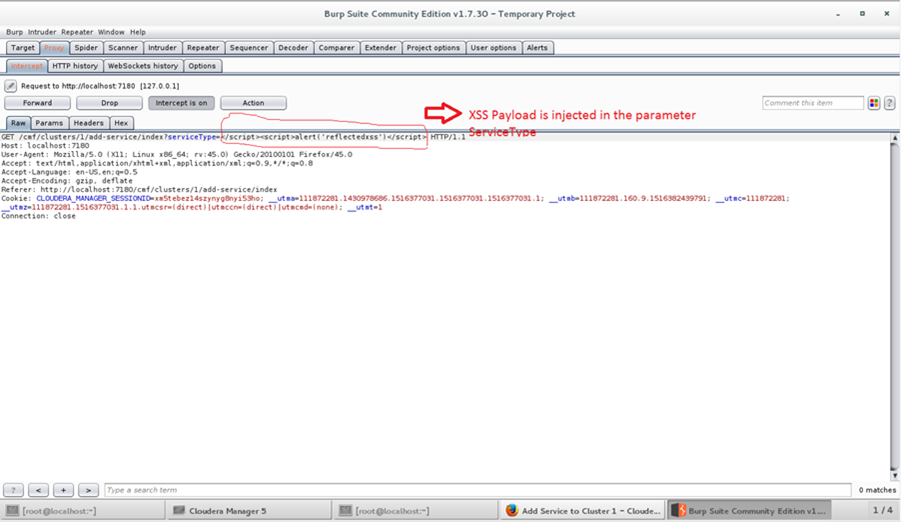
Switch of the interception in burp and come back to the browser. Will see the XSS payload executed as shown in the below image.

The vulnerability can be reproduced by accessing the following URL
directly.http://localhost:7180/cmf/clusters/1/add-service/index?serviceType=
Please note you have to log in to the Cloudera Manager with above mentioned credentials. Replace the IP of the Cloudera Manager instead of localhost if you are accessing remotely.
